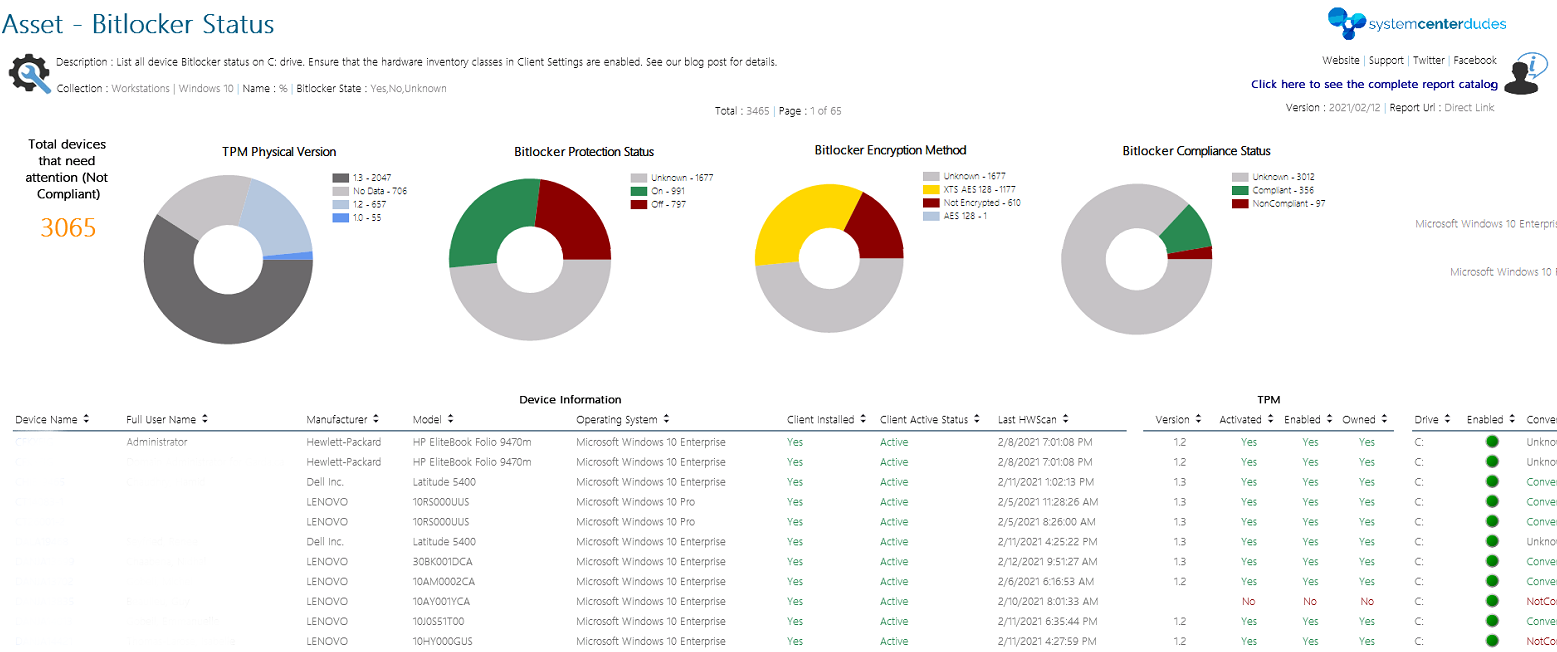

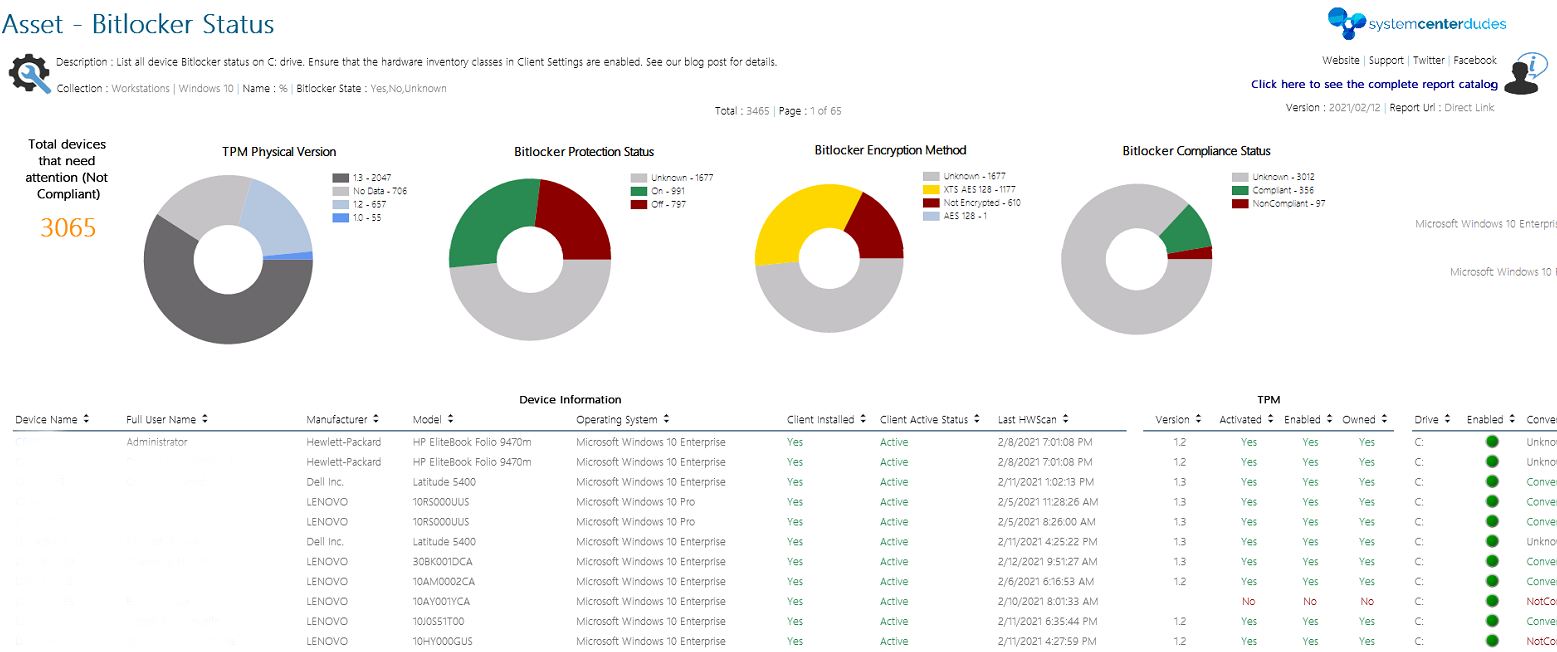
If you’ve been using BitLocker in your organization, you probably receive some requests from your security department to monitor the Bitlocker status of a device if it gets stolen. One of them is a free SCCM Bitlocker Report and a free Power BI Dashboard that we’ve done just for you but there’s a couple of ways to achieve this.
#1 – MBAM
The first and recommended one would be to use Microsoft BitLocker Administration and Monitoring (MBAM). However, this tool is not free, you need to have Microsoft Desktop Optimization Pack (MDOP). Microsoft has also announced that the actual MBAM 2.5 version is getting deprecated soon (Extended support on July 2019). So we’ll skip this one for now.
#2 – Configuration baseline
The second solution would be to use a configuration baseline in SCCM to monitor BitLocker and report the configuration baseline status using a report. This is a good solution but you’ll need to create a baseline based on a script and deploy it to all your computers. If you’re not familiar with the configuration baseline and want a quicker,
#3 – SCCM Bitlocker Report
Another solution would be to use a built-in SCCM Bitlocker report… but there’s none in the console. The good news is that we’ve created one for you and giving it for free just because we think you’re awesome!

There are 2 small
#4 – SCCM Power BI Dashboard
If you’re using Power BI in your organization, we’ve also created a free Bitlocker Compliance Dashboard that you can use.
As for the SSRS report, you need to enable Bitlocker inventory classes in your Hardware inventory. If your inventory is already configured for Bitlocker, jump to the download section.
HOW TO ENABLE Bitlocker INVENTORY for SCCM Bitlocker Report
Select the Client Settings that apply to your
- Open the SCCM Console
- Go to Administration / Client Settings
- Right-Click your Default Client Setting, select Properties

- Click on Hardware Inventory
- Click on Set Classes

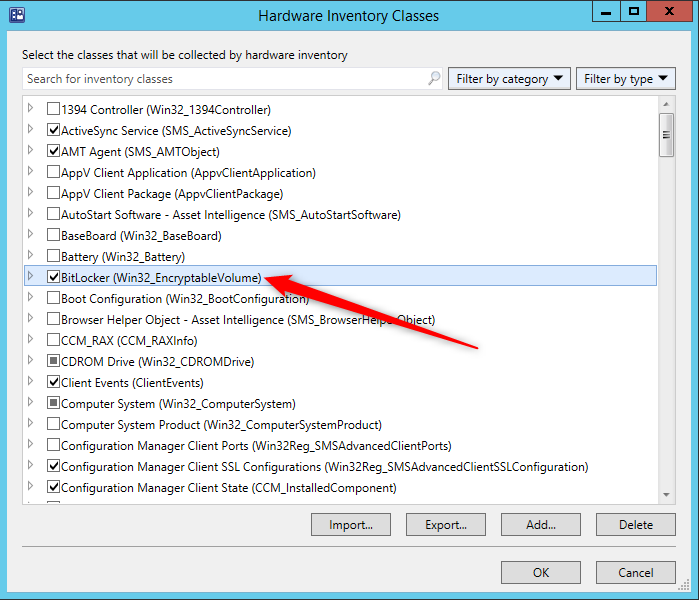
- Ensure that Bitlocker (Win32_EncryptableVolume) is enabled
- Ensure that both TPM (Win32_Tpm) and TPM Status (SMS_TPM) classes are also enabled
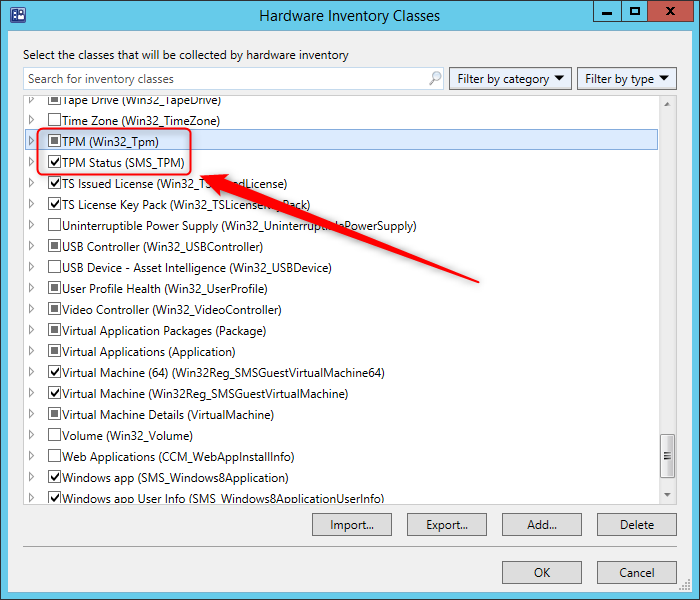
- Close the Hardware inventory class window by clicking ok.
Bitlocker Inventory Verification
Now that our classes are enabled, trigger a Machine Policy Retrieval & Evaluation Cycle (to have the latest Client Settings) followed by
- In the SCCM Console
- Right-Click your device, select Start / Resource Explorer
- Confirm that you have Bitlocker listed
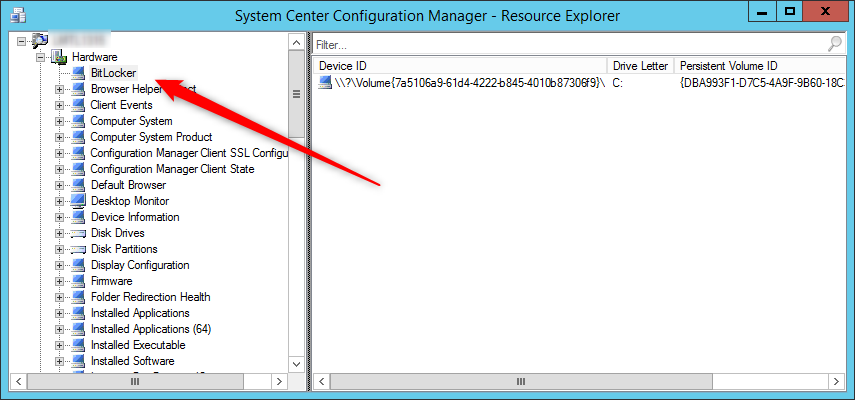
Free SCCM Bitlocker Reports
Now that you’ve confirmed that the inventory is working, the last thing you need to do is monitoring using reporting.
SSRS
- Download the RDL File from our product page | Asset – Bitlocker Status
- Upload the report to your Reporting Point and change the data source
- Run the report

You can download this free report by visiting our product page. The Asset – Bitlocker Status report is free to download.















Brian Larsen
05.15.2019 AT 12:33 PMJeff Huffman
04.15.2019 AT 11:58 AMTony
01.31.2019 AT 03:46 PMJason
01.24.2019 AT 06:42 PMLauren Layton
05.24.2019 AT 12:48 PMDanny
03.15.2019 AT 10:31 AMsteve
01.31.2019 AT 03:33 PMAnthony Reyna
01.24.2019 AT 01:07 PMMike
01.17.2019 AT 10:29 PMSimon
01.16.2019 AT 09:40 AMsathish
01.16.2019 AT 02:13 AMsathish
01.14.2019 AT 05:53 PMBenoit Lecours
01.15.2019 AT 08:00 AMStian M. Olsen
01.15.2019 AT 10:37 AM